What small-to-medium-sized businesses need to know about building incident response plans
Why should you care about Incident Response Plans?
Cyberattack, security breach, ransomware…It’s almost impossible to go more than a few hours without hearing these ominous words in the news or in business conversations. COVID-19 and the Russian invasion of Ukraine have heightened our nation’s fear of damaging cyberattacks, and deservedly so.
The rate, intensity, and resulting damages caused by security breaches and ransomware are increasing at a mind-boggling rate. According to Cybersecurity Ventures, ransomware attacks happened every 11 seconds in 2021, with cybercrime damages expected to reach $10.5 trillion a year by 2025.
In response to Russia’s invasion of Ukraine, the US Cybersecurity and Infrastructure Security Agency (CISA) released a cybersecurity guide called ‘Shields Up’ to help organizations be better prepared to handle cyber threats.
And, the security breach threats are not just for big companies. All organizations, large and small, must be prepared. Homeland Security Secretary Alejandro Mayorkas revealed to the US Chamber that small businesses account for 50-75% of ransomware attacks.
Prevention is critical to minimize the potential risk of data breaches. And these alarming trends in cyberattacks on businesses of all sizes help emphasize the need to be prepared.
What is an Incident Response Plan?
An Incident Response Plan (IRP) is a documented policy that details structured processes and steps an organization should follow to aid in the detecting, responding, and recovering from a cyber incident such as ransomware.
The Incident Response (IR) process based on the NIST 800-61 framework includes several phases: pre-planning; detection & analysis; containment, eradication, & recovery; and post-incident analysis. While there are many guidelines for developing an Incident Response Plan, your IRP should be customized to align with your organization’s priorities, response capabilities, and risk tolerance.
Why is it essential to have an Incident Response Plan?
Preparing an Incident Response Plan before a cyber incident helps organizations in many ways, including;
- Helps expose weaknesses and network vulnerabilities through a pre-planning risk audit
- Provides a step-by-step response plan that results in swift actions, critical to minimizing damage
- Guides decisions based on a pre-determined set of rules
- Maximizes an organization’s resilience to cyberthreat damage by establishing critical control and recovery processes
- Preserves essential knowledge and helps organizations respond in a repeatable manner which is optimized with each practice and test run
- Identifies Incident Response team members, along with roles and responsibilities to eliminate guesswork, confusion, and lost time
- Defines the what-who-when communication strategy for internal and external stakeholders, so all parties are notified at the appropriate time with the appropriate information
- Helps reduce liability by showing responsibility and accountability for actions during any forensic analysis from media, board members, regulatory, or other third-party entities
- Helps organizations achieve compliance with industry-specific regulatory requirements
It is important to note that an Incident Response Plan is an evolving or ‘live’ plan. With continuous testing, feedback, and analysis cycle, the incident response plan provides a more robust and effective defense against constantly evolving cyber threats. Organizations should refresh the plan often with vulnerability tests and risk assessments completed quarterly or annually to uncover new threats.
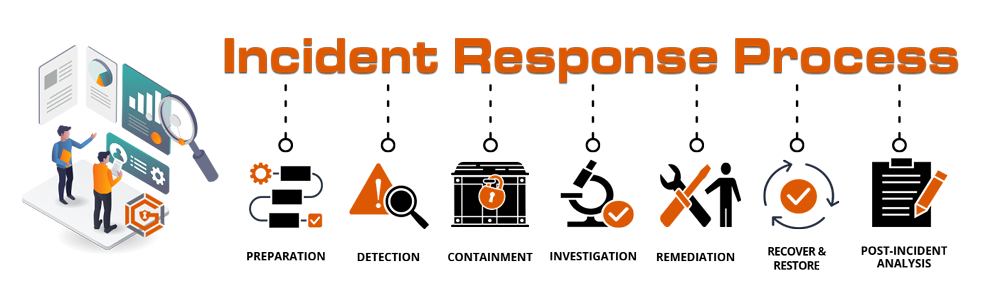
What are the steps in the Incident Response Process?
Based on the NIST framework, GlacisTech utilizes a 7-step Incident Response Process which includes:
1. Preparation
This phase of the incident response process is one of the most critical steps and includes;
Completing an in-depth risk assessment to uncover vulnerabilities and weaknesses
- Implementing required software tools to shore up potential weaknesses, updating and patching where necessary
- Identifying Incident Response Plan team and documenting roles and responsibilities
- Preparing or updating organizational security policies and processes- including the detailed incident response steps, disaster recovery, access controls, cyber insurance, and documenting the organization’s policy on negotiating and paying ransom demands
- Training employees through proven cyber awareness training techniques
- Running penetration tests, mock drills, and table-top exercises to verify IRP system tools and processes
2. Detection
The second phase of the IR process is discovering and detecting a cyber incident or breach. Detection is accomplished through a set of AI-empowered and advanced detection tools, in addition to 24/7 monitoring of the network to spot anomalies and potential intrusions. Detection is integrated with automated alert systems that immediately notify the appropriate stakeholders of a potential security breach and automatically initiate analyzing and classifying the incident in preparation for the next step. Document all detection steps and details for post-incident reporting.
3. Containment
The third phase of the incident response process involves isolating and quarantining the malware to mitigate damage. It is critical to preserve all physical and digital evidence for forensic analysis, so containment of the impacted systems is quarantined in a controlled environment for further investigation. Communication to affected parties is initiated based on the policies and processes developed in the Preparation phase based on initial analysis of the impact. Document all containment steps and details for post-incident reporting.
4. Investigation
In the quarantined, controlled environment, further investigation of the cyber incident is conducted to identify a baseline of normal activity, collect data points on anomalies, identify attacking host and threat actors, analyze critical services and stakeholders impacted, and conduct communication with the threat actor based on the documented policies and procedures to determine the remediation strategy and tactics required. Document all investigation steps and details for post-incident reporting.
5. Remediation
The remediation strategy and tactics utilized will depend on the specific incident, systems and critical functions impacted, and potential damage assessments. Once all evidence is documented for forensic analysis, the removal or eradication of all elements of the incident proceeds. This could include removing all malware, securing access controls, and resetting passwords. Document all remediation steps and details for post-incident reporting.
6. Recover & Restore
Based on the disaster recovery processes designed and documented in the preparation phase of the IR process, begin recovering data and systems from protected backups to restore normal operations as quickly as possible. This phase will also include any additional updates, patches, and retesting to ensure the systems won’t be impacted again. Document all recover and restore steps and details for post-incident reporting.
7. Post-Incident Activity
Once the cyber incident is remediated, and under control, a series of post-incident activities are completed and could include:
- Collection and organization of all documentation from previous steps for post-incident reporting – this could consist of forensic investigations, reports to regulatory agencies, law enforcement, board, executive stakeholders, or other entities
- Conduct internal reviews to examine data and garner information on what worked and where improvements to policies, processes, and toolsets could help prevent and mitigate future exposures
- Conduct follow-up tests of anti-malware software, content & spam filters, and advanced protection systems
- Perform software updates and patches as necessary based on insights gleaned from post-incident activities
- Review incident response plan and update as necessary based on insights
It’s important to note that each step of the incident response process should contain feedback loops to provide learnings in a non-linear manner. In other words, organizations should view the process as an ‘always evolving’ process for doing, learning, and tweaking to ensure a robust and up-to-date process that provides organizational resilience to cyber threats. After all, bad actors continue to evolve their methods. And cybercrime is a highly organized, efficient, and lethal business model that mandates 24/7 organizational vigilance to prevent falling prey.
[activecampaign form=9]
Who should have an Incident Response Plan?
If your organization has sensitive data or data critical to the function of your business, you need an incident response plan.
Ransomware-as-a-service (RaaS) is a thriving and lethal business model that can threaten any organization- any size, any industry, any size. As proven by recent statistics from the FBI and Homeland Security, the size of your organization doesn’t matter. Ransomware and cybercrime can impact small, medium, and enterprise-level organizations with devasting results.
Want to know more about developing an Incident Response Plan for your organization?
We are the experts! Give us a call at 469-522-2022, or fill out the quick inquiry form below for a free consultation.
[activecampaign form=11]
About GlacisTech
GlacisTech is a managed service provider (MSP) and managed security solution provider (MSSP) for small to medium-size businesses in the Dallas and North Texas region. GlacisTech helps businesses grow by providing innovative, state-of-the-art IT solutions that allow its customers to reduce network downtime, increase operational efficiencies, and cost-effectively scale their IT to meet the demands of their growing businesses.
GlacisTech’s suite of Worry-Free IT services includes managed IT, cybersecurity, virtual CIO, managed compliance & remediation, and cloud services.
Glacis Technologies, Inc
1130 East Arapaho, Suite 184
Richardson, TX 75081
24/7 Customer Support 469-522-2022
ITsupport@GlacisTech.com







