Ransomware Attack – Are you Next?
Small and Medium-Sized Businesses (SMBs) are the backbone of the US economy, employing 60 million people in 31.7 million businesses. But these SMBs are under attack.
While ransomware has been a critical challenge for some time, hackers have been increasingly targeting small to medium-sized businesses since early 2020 and the start of the COVID19 pandemic. A recent report by the Cybersecurity and Infrastructure Security Agency (CISA) states that attacks against smaller businesses comprise up to 50-75% of ransomware attacks.
The cost of ransomware hits SMBs hard
Ransomware is a cybersecurity attack where hackers take your entire network hostage by encrypting its data and demanding payment, usually in millions of dollars. Only the hackers may have a decryption key, and you are never guaranteed to get it even after paying the ransom amount.
The cost of ransomware attacks and the demand values are increasing, and SMBs are paying the price. In 2021, the average payout by a mid-sized organization was $170,404 and
Cybercrime Magazine says nearly 60% of small and medium businesses shut down after six months of a cyberattack.
Why are small and medium-sized businesses so vulnerable to ransomware attacks? It may be that cash-strapped SMBs often do not have a viable cybersecurity policy in place, which leaves them vulnerable to these attacks.
Sophisticated and evolving ransomware attacks demand a multi-layered defense
In a digital-first world, there will be risks. There is never a 100% guaranteed method to safeguard your business from a ransomware attack. But there are proven tips and precautions you can take to reduce your chances of getting compromised.
GlacisTech, a top cybersecurity managed service provider (MSP), recommends a multi-layer approach to protect your organization’s critical assets. Greg Murff, GlacisTech President and CEO, says, “Layering advanced solutions together provides much stronger security protection for SMBs than any single layer or toolset.”
How can businesses protect themselves from ransomware attacks?
GlacisTech’s approach for cybersecurity and data protection falls into three phases:
Prevent as much as possible
Preventative measures start with a complete network risk assessment to uncover any risks on the network and connected devices. GlacisTech recommends performing this risk assessment at least once a year to stay ahead of evolving and highly sophisticated cyber tactics.
Additional preventative measures include a suite of tools such as:
- AI-based antivirus software
- Advanced detection software
- User access controls
- Content filters that scrub all web traffic
- Advanced email scanning technology
- Managed firewall to protect the network’s perimeter.
React as soon as possible
When a malicious attack infiltrates your network, a quick reaction is vital to quarantining the malware and mitigating damage. For GlacisTech clients, this happens immediately as all the advanced preventative tools are integrated directly with GlacisTech’s ticketing system.
Client networks are scanned and monitored 24/7 with AI-based advanced detection tools. When any anomaly is detected, a ticket is opened immediately, and appropriate actions are taken to secure the network. The actions taken are pre-determined based on a security incident response plan for the quickest reaction and best outcome.
Recover and restore when needed
If a network has been infected and malicious activity has impacted the integrity of the network, the disaster and recovery process help recover and restore client data to its pre-infection state.
GlacisTech’s approach ensures a complete, end-to-end security posture for clients on a managed service program. But what can businesses do to help protect your organization’s valuable assets?
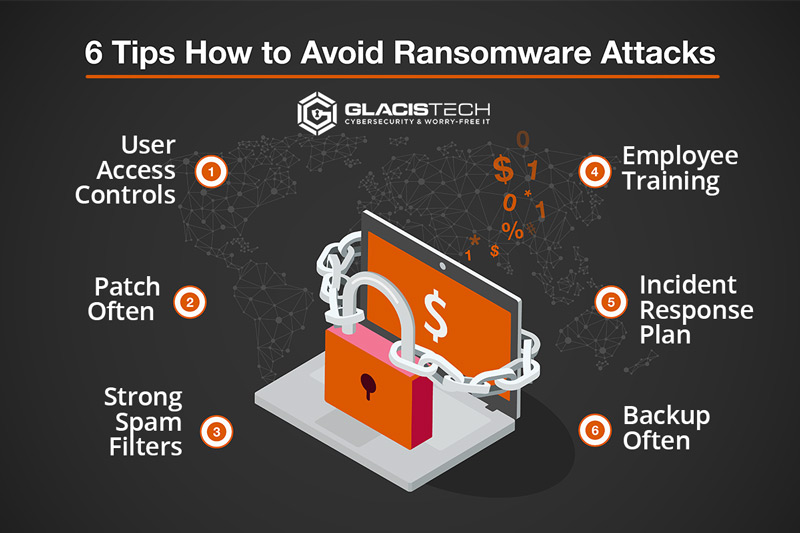
Six proven tips to help protect your business from ransomware attacks
Phase I- Prevent
Tip #1: Configure and deploy user access controls
Ransomware attacks are often launched from phishing and social engineering scams to steal user data such as credentials. In fact, stolen credentials account for almost 90% of data breaches.
Once a cybercriminal has stolen credentials, gaining access to valuable organizational data isn’t difficult without user access controls.
Access controls, or identity and access management (IAM), helps ensure that data is available only to authorized personnel and helps mitigate the risks of hackers getting their hands on your data. Multi-factor authentication (MFA) is a method of access control that validates a combination of factors to access a platform, system, file, directory, or network. Rather than simply requesting a username and passcode, MFA requires one or more additional verification factors (such as a PIN or answers to security questions), thus decreasing the possibility of a successful ransomware attack.
Tip #2: Enable advanced detection & patch often
Implement advanced protection security programs to continually scan for security breaches and alert you of incoming threats. Licensed antivirus, anti-malware software, and network security programs provide an enhanced level of protection in detecting suspicious network activity, blocking virus and malware attacks, and limiting access to your network. Additionally, ransomware code often targets known vulnerabilities, so keeping software and firmware updated and patched is a critical step in a layered approach to security.
Tip #3: Enable strong spam filters
Email is still one of the most used methods of infiltrating a network. To reduce the risk of phishing emails that attempt to obtain sensitive information, install and enable strong spam filters that immediately detect possible spam and quarantine the message. Scan all incoming and outgoing emails to detect threats and filter executable files using technologies such as Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent spoofing.
Additionally, educate your employees on how to spot and avoid malicious emails and to exercise caution when opening emails.
Tip #4: Educate and train employees on cybersecurity awareness
Almost 90% of all breaches start with an email, most of which are phishing for credentials. Even with the most advanced threat protection and AI-based spam and content filters, 10% of malicious activity will still get through.
Why? Because bad actors have decided that it’s easier to trick a human than to bypass very sophisticated technology. And the sad truth is, they are right.
This is why educating all employees and providing them with cybersecurity awareness tools is critical to locking down your assets. Our experiences show that most of our clients who suffered from a data breach were due to human negligence and error.
Employees have a lot on their plate, and they hurry to get things accomplished. And the complex tricks used by bad actors are very difficult to differentiate potential scams from regular email correspondence. Innocently clicking on a link can unknowingly open up backdoors of their company networks for cybercriminals to continuously monitor and finally stage a successful attack.
As your company’s first line of defense, your employees may be the first to spot suspicious activity. And with proper training, they can always remain vigilant and respond according to the security protocols you create as part of your company-wide security incident response plan.
Phase II: React
Tip #5: Develop a security incident response plan
As many industry experts will tell you, prevention is the best way to protect your organization from ransomware attacks. But, in today’s landscape, the question isn’t ‘if’ you will be the victim of a cyber-attack of some form – it is ‘when’ you will be the victim.
That’s why having a security incident response plan is critical and could be the key to surviving the attack or closing your doors.
A security incident response plan is a set of steps and processes that aids in detecting, responding, and recovering from a cyber incident such as ransomware. The incident response plan can be developed internally for organizations with internal cybersecurity experts. For organizations that lack this in-house expertise, it’s best to partner with a qualified managed security service provider to ensure the best possible outcomes in case of an attack.
To learn more about creating a security incident response plan, talk to a Managed Service Provider (MSP) with expertise in cybersecurity.
Phase III: Recover & Restore
Tip #6: Make regular backups of your data
Backing up your data should be one of the first priorities of your IT department to prepare for any worst-case scenario. While recovering backup data may not be an easy or instant solution, it can mitigate the damage in the unfortunate event of a ransomware attack. We suggest our clients make multiple backup copies of their data since malware often targets and holds hostage data backups. Depending on how your backups are configured, you may end up saving on ransom payments but suffer some downtime, which could last anywhere between a few days up to a month or more.
Hackers are getting smarter day by day, and if they figure out your backup data is stored on the network (which most companies do), it will be encrypted first! Hence, you should store backup data offline on externally attached hard drives for easy access.
Last but not least
None of these methods provide a 100% guarantee to safeguard your system against ransomware attacks. However, they do increase the security of your network and mitigate the costly risk of a data breach and ransomware attack. By partnering with a dedicated managed IT services provider like GlacisTech, you can always stay one step ahead in hardening your network security.
What to do in the case of a ransomware attack?
Likely you should be prepared for a worst-case scenario, but if it happens, there are a few things we strongly suggest you do immediately:
- Turn off the entire network, including all systems that may have been compromised.
- Do not talk to the hacker in an attempt to negotiate for a lower ransom payment. It’s illegal.
- Report the crime to the FBI and local law enforcement authorities.
- Connect with your managed IT services provider immediately to quarantine and initiate remediation protocols.
GlacisTech is a managed service provider (MSP) that understands technology – and how to help you build a layered and proactive cybersecurity strategy. Whether you have just been impacted by ransomware or want to start building a cybersecurity policy that protects you from future attacks, we can help.
Get started with a free IT Risk Assessment today.
About GlacisTech
GlacisTech is a managed service provider (MSP) and managed security solution provider (MSSP) for small to medium-size businesses in the Dallas and North Texas region. GlacisTech helps businesses grow by providing innovative, state-of-the-art IT solutions that allow its customers to reduce network downtime, increase operational efficiencies, and cost-effectively scale their IT to meet the demands of their growing businesses.
GlacisTech’s suite of Worry-Free IT services includes managed IT, cybersecurity, virtual CIO, managed compliance & remediation, and cloud services.
Glacis Technologies, Inc
1130 East Arapaho, Suite 184
Richardson, TX 75081
24/7 Customer Support 469-522-2022
ITsupport@GlacisTech.com







One Comment